ClearlyIP’s Tips and Tricks
In ClearlyIP we are very serious when it comes to security, and we are way more than strict and precautious when it comes to our own infrastructure and therefore our customer’s peace of mind and one of the many tools we use for this is APIBAN.
APIBAN is an extremely simple yet powerful tool to block unwanted IPs that are known for doing “bad” SIP traffic (or attacking VoIP systems). The key component of APIBAN is the data shared across many honeypots. The honeypots are in charge of extracting valuable information from any SIP attack making APIBAN an alerting method about IP addresses sending bad traffic to SIP servers
APIBAN’s key features are: demands little CPU/Memory use, uses a simple HTTP GET option (we can work with the Linux commands “wget” or “curl”) to retrieve the information of the offending IP Addresses performing attacks to the SIP protocol. It can also work with any firewall that supports IPSET.
In this article, we will present the case in which we would like to secure our server that is running Asterisk or FreePBX or Kamailio or OpenSIPS, or whatever VoIP solution running on a Linux server with SIP protocol. For this case, we will use the pre-compiled iptables client, written in “GO” language.
The first thing to do is to get a key associated with an email [1]
Then follow the quick and easy instructions specified on their Github site [2]:
- Create the folder /usr/local/bin/apiban
- Download apiban-iptables-client to /usr/local/bin/apiban/
- cd /usr/local/bin/apiban
- wget https://github.com/palner/apiban/raw/v0.7.0/clients/go/apiban-iptables-client
- Download config.json to /usr/local/bin/apiban/
- cd /usr/local/bin/apiban
- wget https://raw.githubusercontent.com/palner/apiban/v0.7.0/clients/go/apiban-iptables/config.json
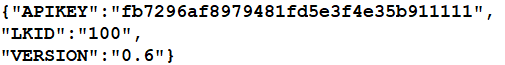
- Update config.json with your APIBAN key, for example:
- Give apiban-iptables-client execute permission
- chmod +x /usr/local/bin/apiban/apiban-iptables-client
- And Test
- ./usr/local/bin/apiban/apiban-iptables-client
Once the client has run we can execute the command iptables -nvL to see the iptables chain (APIBAN) and offending IPs added to our firewall
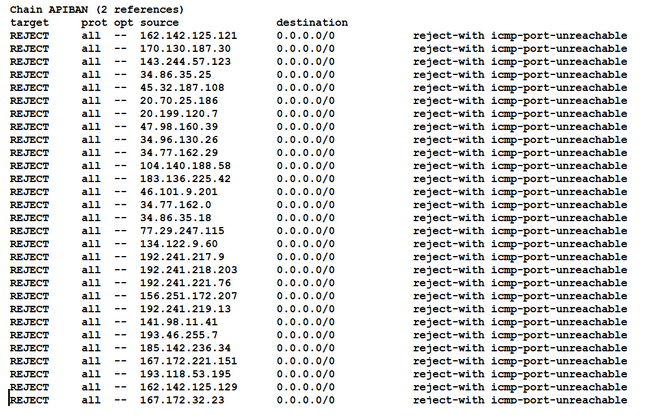
Additionally, we can look at the APIBAN client log to see the list of the up-to-date offending IP addresses that are being blocked. The logs are stored in the file /var/log/apiban-client.log. At the moment of writing this article we noticed there are 1114 IP addresses blocked!
If we would like to automate this process, we can create a cron job that will execute the client every 10 minutes as follows.
# update apiban iptables
*/10 * * * * /usr/local/bin/apiban/apiban-iptables-client >/dev/null 2>&1
For more information, you can visit https://www.apiban.org/doc.html
[1] https://apiban.org/getkey.html[2] https://github.com/palner/apiban/tree/master/clients/go

